Security, privacy, compliance, and trust▸
Azure pricing Service Level Agreements, and Lifecycles▸
The AZ-900, Microsoft Azure Fundamentals , certification exam is designed for candidates looking to demonstrate foundational level knowledge of cloud services and how those services are provided with Microsoft Azure. The exam is intended for candidates with non-technical backgrounds, such as candidates involved in selling or purchasing cloud-based solutions and services.
| AZ-900 Study Areas | Weights |
|---|---|
| Understand cloud concepts | 15-20% |
| Understand core Azure services | 30-35% |
| Understand security, privacy, compliance, and trust | 25-30% |
| Understand Azure pricing, service level agreements, and lifecycle | 20-25% |
Cloud Computing is the delivery of computing services—servers, storage,
databases, networking, software, analytics, intelligence and more—over the
internet (the cloud), enabling faster innovation, flexible resources, and
economies of scale. You typically pay only for cloud services you use,
helping lower your operating costs, run your infrastructure more
efficiently, and scale as your business needs change.
The company providing these services is referred to as a cloud provider.
Some example providers are Microsoft Azure, Amazon Web Services (AWS), and
the Google Cloud Platform (GCP).
Cloud services have characteristics and considerations, some of which are outlined and explained below:
Capital Expenditure (CapEx) - This is the up front spending of money on physical infrastructure, and then deducting that up front expense over time.
Operational Expenditure (OpEx) - This is spending money on services or products now and being billed for them now. You can deduct this expense in the same year you spend it. There is no up front cost, as you pay for a service or product as you use it.
Today, organizations can sign up for a service from a cloud provider to get up and running without the need for a significant investment into up front costs.
A typical on-premises datacenter includes costs such as: Server costs , Storage costs, Network costs, Backup and archive costs, continuity and disaster recovery costs, datacenter infrastructure costs, Technical personnel.
Benefits of CapEx
With capital expenditures, you plan your expenses at the start of a
project or budget period.
Benefits of OpEx
Demand and growth can be unpredictable and can outpace expectation, which
is a challenge for the CapEx model as shown in the following graph. OpEx
is particularly appealing if the demand fluctuates or to try a new product
or service.
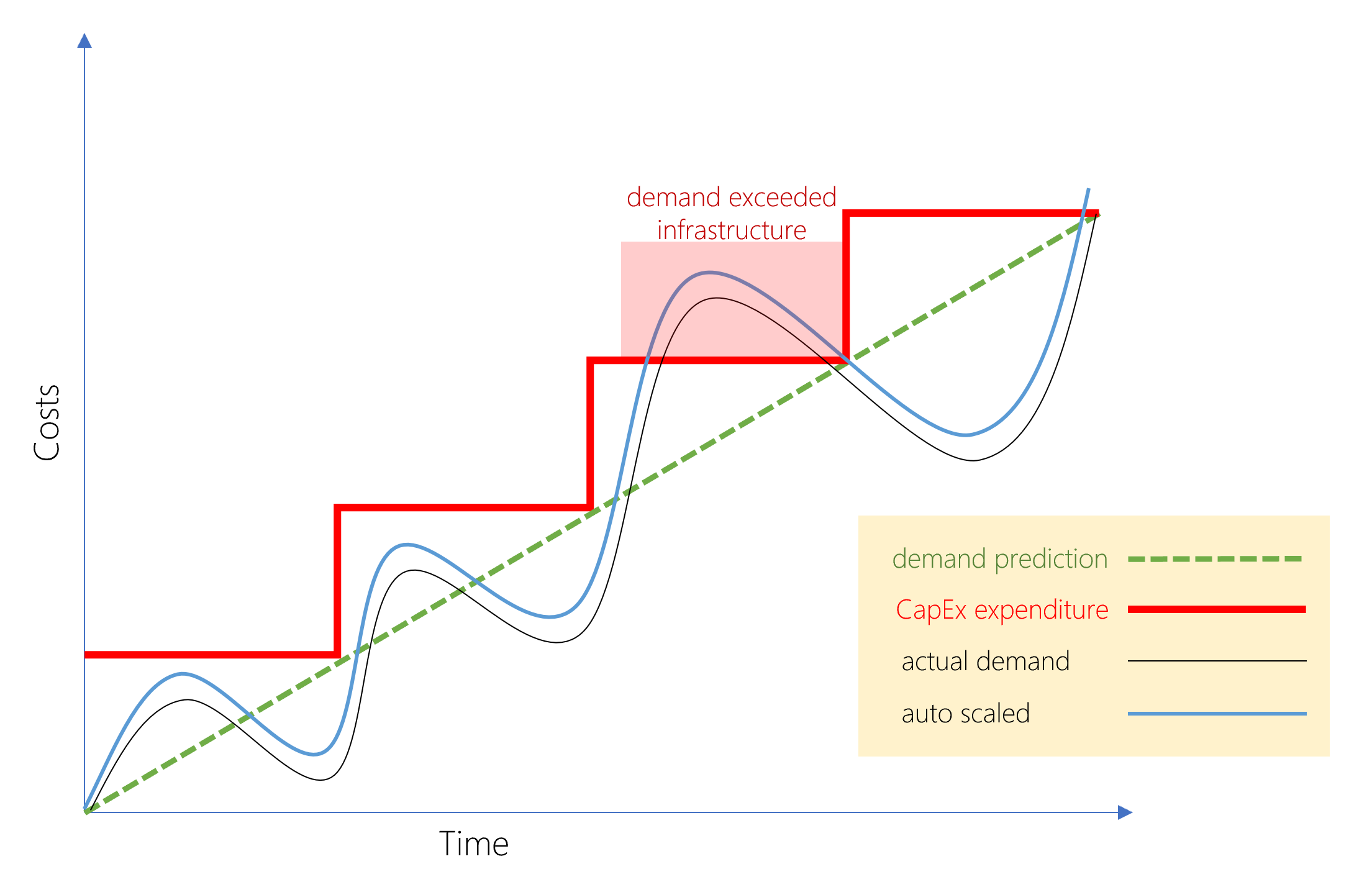
Users only pay for the resources that they use. A consumption-based model has many benefits, including:
There are three different cloud deployment models.
A public cloud is owned by the cloud services provider. This is the most common deployment model. Public cloud models have the following characteristics:
Advantages:
Disadvantages:
A private cloud is owned and operated by the organization that uses the resources from that cloud. Private cloud models have the following characteristics:
A use case scenario for a private cloud are:
Advantages:
Disadvantages:
A hybrid cloud combines both public and private clouds, allowing you to run your applications in the most appropriate location. Hybrid cloud models have the following characteristics:
Advantages:
Disadvantages:
When talking about cloud computing services, there are three major categories: IaaS, SaaS, and PaaS.
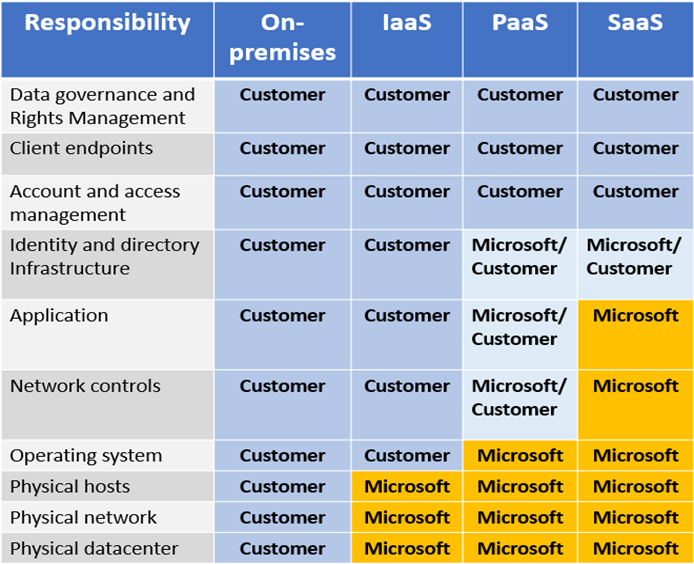
Shared responsibility model
Depending on the service you are using, the cloud provider is responsible
for some aspects of the workload management, and the customer or end user
is responsible for other aspects of the workload management, and in some
cases, both share a responsibility.
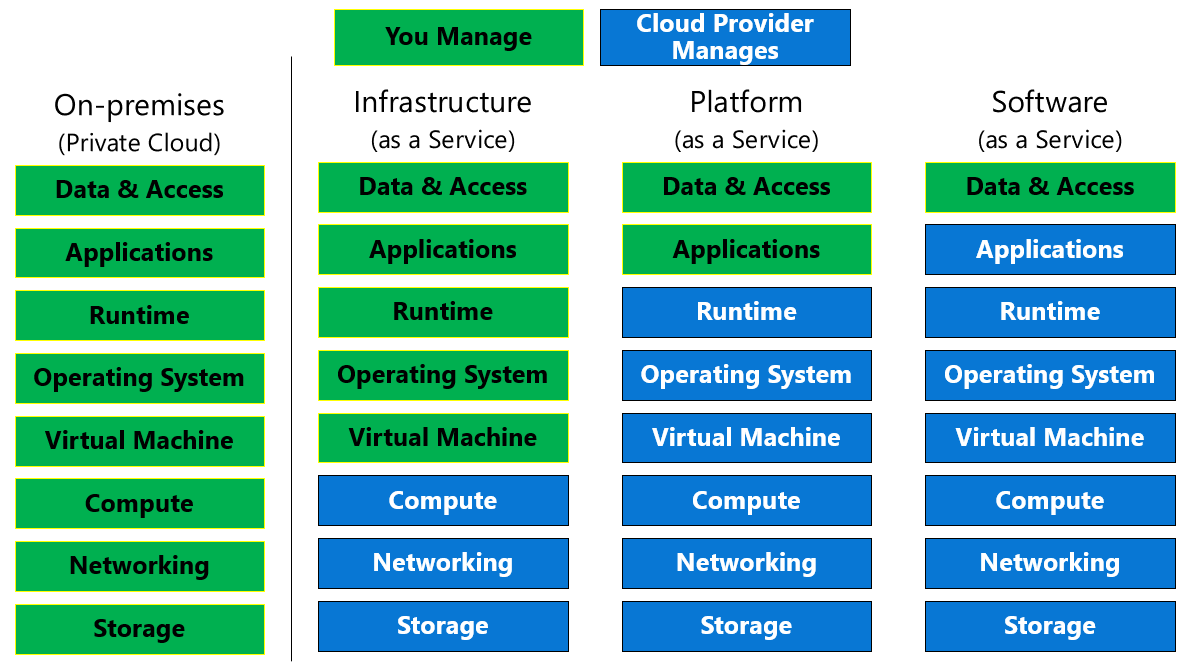
Infrastructure as a Service (IaaS) is the most basic category of cloud computing services. You rent IT infrastructure servers and virtual machines (VMs), storage, networks, and operating systems from a cloud provider on a pay-as-you-go basis.
IaaS characteristics
Common IaaS usage scenarios
Advantages
Disadvantages
Platform as a Service (PaaS) provides an environment for building, testing, and deploying software applications.
PaaS characteristics
Common PaaS usage scenarios
Advantages
Disadvantages
Software as a Service (SaaS) is software that is centrally hosted and managed for the end customer. It allows users to connect to and use cloud-based apps over the internet.
SaaS characteristics
Common SaaS usage scenarios
Common examples are email, calendars, and office tools such as Microsoft Office 365.
Advantages
Disadvantages
Azure Benefits
Be future ready - Continuous innovation from Microsoft supports your development today, and your product visions for tomorrow.
Build on your terms - You have choices. With a commitment to open source, and support for all languages and frameworks, build how you want, and deploy where you want to.
Operate hybrid seamlessly - On-premises, in the cloud, and at the edge—we’ll meet you where you are. Integrate and manage your environments with tools and services designed for hybrid cloud.
Trust your cloud - Get security from the ground up, backed by a team of experts, and proactive compliance trusted by enterprises, governments, and startups.
You can purchase Azure access directly from Microsoft by signing up on the
Azure website, or through or Microsoft partner. You can also purchase
Azure access through a Microsoft partner.
If you're new to Azure, you can sign up for a free account on the Azure
website to start exploring at no cost to you.
The Azure free account includes free access to popular Azure products for
12 months, a credit to spend for the first 30 days, and access to more
than 25 products that are always free.
To sign up, you need a phone number, a credit card, and a Microsoft or
GitHub account. Credit card information is used for identity verification
only. You won't be charged for any services until you upgrade.
A region is a geographical area on the planet containing at least one, but potentially multiple datacenters that are in close proximity and networked together with a low-latency network. A few examples of regions are West US, Canada Central, West Europe, Australia East, and Japan West. At the time of writing this, Azure is generally available in 55 regions and available in 140 countries.
Special Azure regions
Each Azure region is paired with another region within the same geography (such as US, Europe, or Asia) at least 300 miles away, which together make a region pair.
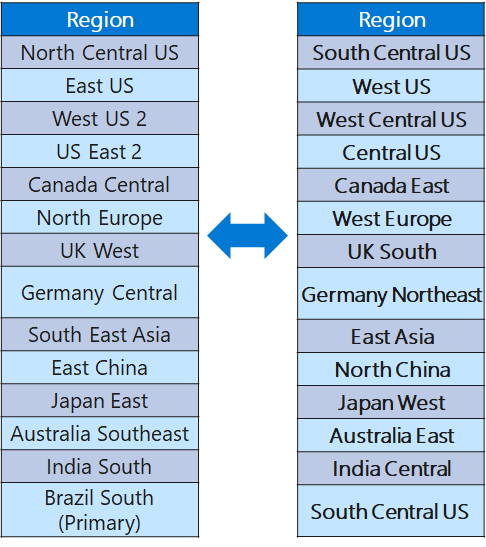
Benefits
Azure divides the world into geographies that are defined by geopolitical boundaries or country borders. An Azure geography is a discrete market typically containing two or more regions that preserves data residency and compliance boundaries.
Benefits
Geographies are broken up into the following areas:
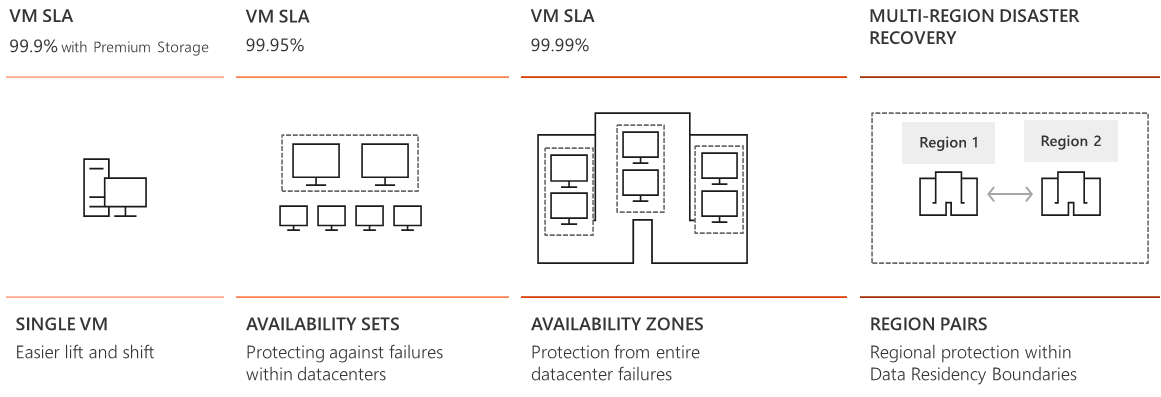
Availability sets are a way for you to ensure your application remains online if a high-impact maintenance event is required, or if a hardware failure occurs.
Availability sets are made up of Update domains (UD) and Fault domains
(FD).
Update domains - When a maintenance event occurs.
Fault domains
provide for the physical separation of your workload across different
hardware in the datacenter.
Availability zones are physically separate locations within an Azure region that use availability sets to provide additional fault tolerance. The availability zones are typically connected to each other through very fast, private fiber-optic networks.
You can co-locating your compute, storage, networking, and data resources
within a zone and replicating in other zones.
Zonal services – you pin the resource to a specific zone
Zone-redundant services – platform replicates automatically across zones
A resource group is a unit of management for your resources in Azure. You can manage and apply the following resources at resource group level:
Remember that when you delete a resource group you delete all resources contained within it.
Considerations
Logical grouping
By placing resources of similar usage, type, or location, you can provide some order and organization to resources you create in Azure.
Life cycle
Resource groups make it easy to remove a set of resources at once which can be useful in non-production environments.
Authorization
Resource groups are also a scope for applying role-based access control (RBAC) permissions.
Create a resource group
Consistent naming convention
Resource groups can be organized in a number of ways.
Azure Resource Manager is a management layer in which resource groups and all the resources within it are created, configured, managed, and deleted.
Azure Hierarchy provides a management layer that enables you to create, update, and delete resoures in your azure subscription.
Hierarchy Layers
[Management groups]
[Subscriptions]
[Resource groups]
[Resources]
Azure compute is an on-demand computing service for running cloud-based applications. It provides computing resources such as disks, processors, memory, networking and operating systems.Typically, cloud services include:
Cloud-based servers that are processing each request and returning a response. Some of common compute powers are VM, Containers and Serverless.
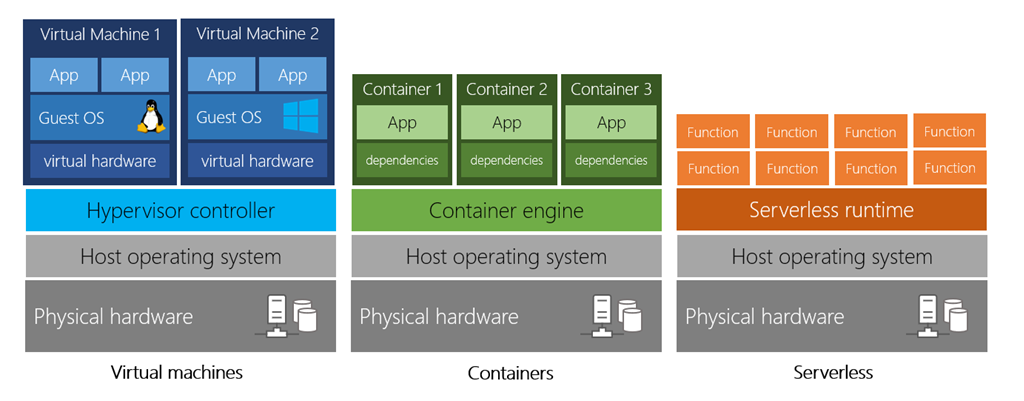
A VM is an emulation of a computer - just like your desktop or laptop you're using now. Each VM includes an operating system and hardware that appears to the user like a physical computer running Windows or Linux. You can then install whatever software you need to do the tasks you want to run in the cloud.
Azure supports a wide range of computing solutions for development and testing, running applications, and extending your datacenter, including Linux, Windows Server, Microsoft SQL Server, Oracle, IBM, and SAP.
Virtual machine scale sets
Virtual machine scale sets are an Azure compute resource that you can use
to deploy and manage a set of identical VMs to support true autoscale and
containerized workloads.
✔️ Walkthrough - Create a virtual machine
Link
Containers provide a consistent, isolated execution environment for applications. They're similar to VMs except they don't require a guest operating system. Instead, the application and all its dependencies is packaged into a "container" and then a standard runtime environment is used to execute the app. The open-source project, Docker, is one of the leading platforms for managing containers. VM virtualises machine, container virtualises OS.
There are two ways to manage both Docker and Microsoft-based containers in Azure.
This architecture is where you break solutions into smaller, independent pieces. For example, you may split a website into a container hosting your front end, another hosting your back end, and a third for storage. This split allows you to separate portions of your app into logical sections that can be maintained, scaled, or updated independently.
✔️ Walkthrough - Deploy Azure Container Instances
Link
🌐 Overview of Azure compute options
Serverless computing lets you run application code without creating, configuring, or maintaining a server. The core idea is that your application is broken into separate functions that run when triggered by some action. This is ideal for automated tasks - for example, you can build a serverless process that automatically sends an email confirmation after a customer makes an online purchase.
An event could be a REST endpoint, a periodic timer, or even a message received from another Azure service.
Azure Functions
Azure Functions are ideal when you're concerned only about the code
running your service and not the underlying platform or infrastructure.
Azure Functions are commonly used when you need to perform work in
response to an event—often via a REST request, timer, or message from
another Azure service—and when that work can be completed quickly, within
seconds or less.
Azure Functions scale automatically, and charges accrue only when a
function is triggered, so they're a solid choice when demand is variable.
Azure Logic Apps
Logic Apps is a cloud service that helps you automate and orchestrate
tasks, business processes, and workflows when you need to integrate apps,
data, systems, and services across enterprises or organizations.
Logic Apps are designed in a web-based designer and can execute logic
triggered by Azure services without writing any code.
Azure Event Grid
Event Grid allows you to easily build applications with event-based
architectures. It's a fully managed, intelligent event routing service
that uses a publish-subscribe model for uniform event consumption.
You can use Event Grid to support your own non-Azure-based events in
near-real time, using custom topics. You can use filters to route specific
events to different endpoints, and ensure your events are reliably
delivered.
✔️ Walkthrough - Implement Azure functions
Link
Cloud providers typically offer storage services that can handle all of these types of data.The advantage to using cloud-based data storage is you can scale to meet your needs. In some cases, the storage can even expand and contract automatically.
You can generally think of data as structured, semi-structured, and
Structured data
Structured data is also known as relational data. The data's schema
defines the table of data, the fields in the table, and the clear
relationship between the two. Structured data can be stored in a database
table with rows and columns. Structured data is easy to enter, query, and
analyze because all the data follows the same format.
Examples of structured data include sensor data or financial
data.
Structured data
Semi-structured data is also known as non-relational or NoSQL data.
Semi-structured data is less organized than structured data.
Semi-structured data is not stored in a relational format, meaning the
fields do not neatly fit into tables, rows, and columns. Semi-structured
data contains tags that make the organization and hierarchy of the data
apparent.
Examples of semi-structured data include books, blogs, and HTML
documents.
Unstructured data
Unstructured data has no designated structure. Unstructured data can hold
any kind of data. Unstructured data is becoming more prominent as
businesses try to tap into new data sources.
Examples Examples of unstructured data include a PDF document, a
JPG image, a JSON file, and video content.
Azure Storage is a service that you can use to store files, messages, tables, and other types of information. Azure Storage is also used by IaaS virtual machines, and PaaS cloud services. Some of the most common storage service types in Azure are disks, files, objects, queues, and tables.
Disk storage provides disks for virtual machines, applications, and other services to access and use as they need, similar to how they would in on-premises scenarios. Disks come in many different sizes and performance levels, from solid-state drives (SSDs) to traditional spinning hard disk drives (HDDs), with varying performance abilities.
Azure Blob storage is Microsoft's object storage solution for the cloud. Blob storage is optimized for storing massive amounts of unstructured data, such as text or binary data.
Blob storage is ideal for:
Azure Files enables you to set up highly available network file shares that can be accessed by using the standard Server Message Block (SMB) protocol. That means that multiple VMs can share the same files with both read and write access. You can also read the files using the REST interface or the storage client libraries.
One thing that distinguishes Azure Files from files on a corporate file share is that you can access the files from anywhere in the world using a URL that points to the file and includes a shared access signature (SAS) token.
File shares can be used for many common scenarios:
The Azure Queue service is used to store and retrieve messages. Queue messages can be up to 64 KB in size, and a queue can contain millions of messages. Queues are generally used to store lists of messages to be processed asynchronously.
For example, say you want your customers to be able to upload pictures, and you want to create thumbnails for each picture. When the customer finishes their upload, write a message to the queue. Then have an Azure Function retrieve the message from the queue and create the thumbnails.
Azure Table storage stores large amounts of structured data. The service is a NoSQL datastore which accepts authenticated calls from inside and outside the Azure cloud. Azure tables are ideal for storing structured, non-relational data. Common uses of Table storage include:
Common uses of Table storage include:
✔️ Walkthrough - Create blob storage
Link
Azure database services are fully managed PaaS database services. Developers can take advantage of industry-leading innovations such as built-in security with automatic monitoring and threat detection, automatic tuning for improved performance, and turnkey global distribution.
Some of the most common data service types in Azure as follows:
Microsoft Azure Cosmos DB is a globally distributed database service that enables you to elastically and independently scale throughput and storage across any number of Azure's geographic regions. It supports schema-less data that lets you build highly responsive and Always On applications to support constantly changing data. You can use Cosmos DB to store data that is updated and maintained by users around the world. It makes it easy to build scalable, highly responsive applications at global scale.
Azure SQL Database is a relational database as a service (DaaS) based on the latest stable version of Microsoft SQL Server database engine.
The Azure Database Migration Service is a fully managed service designed to enable seamless migrations from multiple database sources to Azure data platforms with minimal downtime (online migrations). The service uses the Microsoft Data Migration Assistant to generate assessment reports that provide recommendations to help guide you through required changes prior to performing a migration. Once you assess and perform any remediation required, you're ready to begin the migration process.
✔️ Walkthrough - Create a SQL database
Link
Azure Marketplace is a service on Azure that helps connect end users with Microsoft partners, independent software vendors (ISVs), and start-ups that are offering their solutions and services, which are optimized to run on Azure. Azure Marketplace allows customers—mostly IT professionals and cloud developers—to find, try, purchase, and provision applications and services from hundreds of leading service providers, all certified to run on Azure.
Azure networking components offer a range of functionality and services that can help organizations design and build cloud infrastructure services that meet their requirements.
Azure Virtual Network enables many types of Azure resources such as Azure VMs to securely communicate with each other, the internet, and on-premises networks. A virtual network is scoped to a single region; however, multiple virtual networks from different regions can be connected using virtual network peering. With Azure Virtual Network you can provide isolation, segmentation, communication with on-premises and cloud resources, routing and filtering of network traffic.
✔️ Walkthrough - Create a virtual network
Link
Azure Load Balancer can provide scale for your applications and create high availability for your services. Load Balancer supports inbound and outbound scenarios, provides low latency and high throughput, and scales up to millions of flows for all Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) applications. You can use Load Balancer with incoming internet traffic, internal traffic across Azure services, port forwarding for specific traffic, or outbound connectivity for VMs in your virtual network.
A VPN gateway is a specific type of virtual network gateway that is used to send encrypted traffic between an Azure Virtual Network and an on-premises location over the public internet. It provides a more secure connection from on-premises to Azure over the internet.
Azure Application Gateway is a web traffic load balancer that enables you to manage traffic to your web applications. It is the connection through which users connect to your application. With Application Gateway you can route traffic based on source IP address and port to a destination IP address and port.
A Content Delivery Network (CDN) is a distributed network of servers that can efficiently deliver web content to users. It is a way to get content to users in their local region to minimize latency. CDN can be hosted in Azure or any other location. You can cache content at strategically placed physical nodes across the world and provide better performance to end users.
The Internet of Things (IoT) is the ability for devices to garner and then relay information for data analysis. There are many services that can assist and drive end-to-end solutions for IoT on Azure. Two of the core Azure IoT service types are Azure IoT Central, and Azure IoT Hub.
IoT Central is a fully managed global IoT software as a service (SaaS) solution that makes it easy to connect, monitor, and manage your IoT assets at scale. No cloud expertise is required to use IoT Central.
Azure IoT Hub is a managed service hosted in the cloud that acts as a central message hub for bi-directional communication between your IoT application and the devices it manages. You can use Azure IoT Hub to build IoT solutions with reliable and secure communications between millions of IoT devices and a cloud-hosted solution backend.
✔️ Walkthrough - Implement the Azure IoT Hub
Link
Open source cluster technologies have been developed, over time, to try to deal with these large data sets. Some of the most common big data and analytic service types in Azure are Azure SQL Data Warehouse, HDInsight, and Data Lake Analytics.
Azure Synapse Analytics (formerly Azure SQL Data Warehouse) is a limitless analytics service that brings together enterprise data warehousing and big data analytics.
Azure HDInsight is a fully managed, open-source analytics service for enterprises. It is a cloud service that makes it easier, faster, and more cost-effective to process massive amounts of data. HDInsight allows you run popular open-source frameworks and create cluster types such as Apache Spark ,Apache Hadoop ,Apache Kafka , Apache HBase ,Apache Storm ,Machine Learning Services . HDInsight also supports a broad range of scenarios such as extraction, transformation, and loading (ETL); data warehousing; machine learning; and IoT.
Azure Data Lake Analytics is an on-demand analytics job service that simplifies big data. Instead of deploying, configuring, and tuning hardware, you write queries to transform your data and extract valuable insights.
Artificial Intelligence, in the context of cloud computing, is based around a broad range of services, the core of which is Machine Learning. Machine Learning is a data science technique that allows computers to use existing data to forecast future behaviors, outcomes, and trends.
For example, when you shop online, machine learning helps recommend other products you might like based on what you've purchased. Or when your credit card is swiped, machine learning compares the transaction to a database of transactions and helps detect fraud.
Some of the most common Artificial Intelligence and Machine Learning service types in Azure are:
Cognitive services are a collection of domain-specific pre-trained AI models that can be customized with your data. They are categorized broadly into vision, speech, language, and search. For more information about each service, see the links in the resources section.
The Azure Machine Learning service provides a cloud-based environment you can use to develop, train, test, deploy, manage, and track machine learning models.
Jupyter notebooks or the Visual Studio Code Tools for AI, make it easy to interactively explore data, transform it, and then develop, and test models.
DevOps (Development and Operations) brings together people, processes, and technology, automating software delivery to provide continuous value to your users. Azure DevOps Services allows you to create, build, and release pipelines that provide continuous integration, delivery, and deployment for your applications. You can integrate repositories and application tests, perform application monitoring, and work with build artifacts.
Some of the main DevOps services available with Azure are Azure DevOps Services, and Azure DevTest Labs.
DevOps Services provides development collaboration tools including high-performance pipelines, free private Git repositories, configurable Kanban boards, and extensive automated and cloud-based load testing.
Lab Services is a service that helps developers and testers quickly create environments in Azure, while minimizing waste and controlling cost. Users can test their latest application versions by quickly provisioning Windows and Linux environments using reusable templates and artifacts. You can easily integrate your deployment pipeline with DevTest Labs to provision on-demand environments.
With App services , you can quickly build, deploy, and scale enterprise-grade web, mobile, and API apps running on any platform. App Services is a platform as a service (PaaS) offering.
Key features
✔️ Walkthrough - Create a web app
Link
You can configure and manage Azure using a broad range of tools and platforms. There are tools available for the command line, language-specific Software Development Kits (SDKs), developer tools, tools for migration, and many others.
The Azure portal is a public website that you can access with any web browser. After you sign in with your Azure account, you can create, manage, and monitor any available Azure services. You can identify a service you're looking for, get links for help on a topic, and deploy, manage, and delete resources. It also guides you through complex administrative tasks using wizards and tooltips.
The dashboard view provides high-level details about your Azure environment. You can customize the portal view as you need by moving and resizing tiles, displaying particular services of interest, accessing links for help and support, and providing feedback. The portal does not provide any way to automate repetitive tasks.
Azure PowerShell is a module that you add to Windows PowerShell or PowerShell Core that enables you to connect to your Azure subscription and manage resources. Azure PowerShell requires Windows PowerShell to function. PowerShell provides services such as the shell window and command parsing.
PowerShell Core is a cross-platform version of PowerShell that runs on Windows, Linux or macOS.
To use it, you would launch PowerShell, sign in to your Azure account using the command Connect-AzureRMAccount, and then issue a command.
Azure CLI is a cross-platform command-line program that connects to Azure and executes administrative commands on Azure resources. Cross platform means that it can be run on Windows, Linux, or macOS. For example, to create a Virtual Machine, you would open a command prompt window, sign in to Azure using the command az login, create a resource group, then use a command.
Azure Cloud Shell is a browser-based scripting environment in your portal. It provides the flexibility of choosing the shell experience that best suits the way you work. Linux users can opt for a Bash experience, while Windows users can opt for PowerShell.
A storage account is required to use the Cloud Shell and you will be prompted to create one when accessing the Azure Cloud Shell.
The Microsoft Azure mobile app allows you to access, manage, and monitor all your Azure accounts and resources from your iOS or Android phone or tablet.
Representational State Transfer (REST) APIs are service endpoints that support sets of HTTP operations (methods), which provide create, retrieve, update, or delete access to the service's resources.
Azure Advisor is a free service built into Azure that provides recommendations on high availability, security, performance, and cost. Advisor analyzes your deployed services and looks for ways to improve your environment across those four areas.
✔️ Walkthrough - Create a Virtual Machine with a template
Link
🌐 Azure quickstart Templates gallery
✔️ Walkthrough - Create a Virtual Machine with PowerShell
Link
✔️ Walkthrough - Create a Virtual Machine with the Command Line Interface
Link
Every system, architecture, and application needs to be designed with security in mind, whether on-premises or in the cloud.
Defense in depth is a strategy that employs a series of mechanisms to slow the advance of an attack aimed at acquiring unauthorized access to data. The objective of defense in depth is to protect and prevent information from being stolen by individuals not authorized to access it. The common principles used to define a security posture are confidentiality, integrity, and availability, known collectively as CIA.
Defense in depth can be visualized as a set of layers, with the Data to be secured at the center. Each layer provides protection so that if one layer is breached, a subsequent layer is already in place to prevent further exposure.
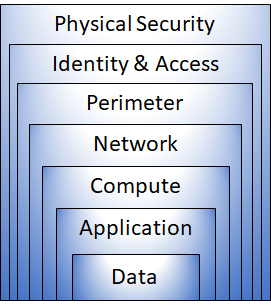
・Physical building security and controlling access to computing hardware
within the data center is the first line of defense.
・With physical security, the intent is to provide physical safeguards
against access to assets. These safeguards ensure that other layers can't
be bypassed, and loss or theft is handled appropriately.
・Control access to infrastructure and change control.
・Use single sign-on and multi-factor authentication.
・Audit events and changes.
・The identity and access layer is all about ensuring identities are
secure, access granted is only what is needed, and changes are logged.
・Use distributed denial of service (DDoS) protection to filter
large-scale attacks before they can cause a denial of service for end
users.
・Use perimeter firewalls to identify and alert on malicious attacks
against your network.
・At the network perimeter, it's about protecting from network-based
attacks against your resources. Identifying these attacks, eliminating
their impact, and alerting you when they happen are important ways to keep
your network secure.
・Limit communication between resources.
・Deny by default.
・Restrict inbound internet access and limit outbound, where appropriate.
・Implement secure connectivity to on-premises networks.
・At this layer, the focus is on limiting the network connectivity across
all your resources to allow only what is required. By limiting this
communication, you reduce the risk of lateral movement throughout your
network.
・Secure access to virtual machines.
・Implement endpoint protection and keep systems patched and current.
・Malware, unpatched systems, and improperly secured systems open your
environment to attacks. The focus in this layer is on making sure your
compute resources are secure, and that you have the proper controls in
place to minimize security issues.
・Ensure applications are secure and free of vulnerabilities.
・Store sensitive application secrets in a secure storage medium.
・Make security a design requirement for all application development.
・Integrating security into the application development life cycle will
help reduce the number of vulnerabilities introduced in code. We encourage
all development teams to ensure their applications are secure by default,
and that they're making security requirements non-negotiable.
・In almost all cases, attackers are after data in a database, on disk
inside virtual machines, on a SaaS application such as Office 365, in
cloud and more.
・It's the responsibility of those storing and controlling access to data
to ensure that it's properly secured. Often, there are regulatory
requirements that dictate the controls and processes that must be in place
to ensure the confidentiality, integrity, and availability of the data.
Azure helps alleviate your security concerns. But security is still a shared responsibility. How much of that responsibility falls on us depends on which model we use with Azure. We use the defense in depth rings as a guideline for considering what protections are adequate for our data and environments.
Microsoft applies a layered approach to security, both in our physical datacenters and across Azure services.
Security of the operational environment is now a concern shared by both cloud providers and customers. By shifting these responsibilities to a cloud service like Azure, organizations can reduce focus on activities that aren't core business competencies.
A Firewall is a service that grants server access based on the originating IP address of each request. Firewall rules also include specific network protocol and port information.
You can create, enforce, and log, application and network connectivity policies across subscriptions, and virtual networks, centrally.
Azure Firewall provides many features, including:
Distributed Denial of Service (DDoS) attacks attempt to overwhelm and exhaust an application’s resources, making the application slow or unresponsive to legitimate users. DDoS attacks can be targeted at any endpoint that is publicly reachable through the internet.
The Azure DDoS Protection service protects your Azure applications by scrubbing traffic at the Azure network edge before it can impact your service's availability.
Basic - The Basic service tier is automatically enabled as part of the Azure platform.
Standard - The Standard service tier provides additional mitigation capabilities that are tuned specifically to Microsoft Azure Virtual Network resources. Protection policies are tuned through dedicated traffic monitoring and machine learning algorithms.
Network Security Groups (NSG) allow you to filter network traffic to and from Azure resources in an Azure virtual network. An NSG can contain multiple inbound and outbound security rules that enable you to filter traffic to and from resources by source and destination IP address, port, and protocol.
| Property | Explanation |
|---|---|
| Name | Unique name of the Network Security Group (NSG). |
| Priority | A number between 100 and 4096. Rules are processed in priority order, with lower numbers processed before higher numbers |
| Source or Destination | Individual IP address or IP address range, service tag, or application security group |
| Protocol | TCP*(Transmission Control Protocal), UDP(User Datagram Protocal), or Any |
| Direction | Whether the rule applies to inbound or outbound traffic |
| Port Range | An individual port or range of ports |
| Action | Allow or Deny |
Application security groups (ASG) enable you to configure network security as a natural extension of an application's structure, allowing you to group virtual machines and define network security policies based on those groups.
Application Security Groups help simplify how you can filter and control network traffic coming into your organization and how that network traffic is allowed to move. They allow you to isolate multiple workloads and provide additional levels of protection for your virtual network in a more easily manageable way.
For example, we have ASGs defined for Web Servers, App Servers, and DB Servers and green and red arrows indicating which network traffic paths are allowable and which are not.
When considering your Azure security solution consider all the elements of defense in depth.
Use Azure DDoS Protection to filter large-scale attacks before they can
cause a denial of service for end users.
Use perimeter firewalls with Azure Firewall to identify and alert on
malicious attacks against your network.
Use NSGs to create rules about inbound and outbound communication at this layer.
You can also combine multiple Azure networking and security services to manage your network security and provide increased layered protection. The following are examples of combined services:
Network security groups and Azure Firewall
Network security groups provide distributed network layer traffic
filtering to limit traffic to resources within virtual networks in each
subscription.
Azure Firewall is a fully stateful, centralized network
firewall-as-a-service, which provides network and application-level
protection across different subscriptions and virtual networks.
Application Gateway WAF and Azure Firewall
WAF is a feature of Application Gateway that provides your web
applications with centralized, inbound protection against common exploits
and vulnerabilities.
Azure Firewall provides inbound protection for non-HTTP/S protocols (for
example, RDP, SSH, FTP), outbound network-level protection for all ports
and protocols, and application-level protection for outbound HTTP/S.
✔️ Walkthrough - Secure network traffic
Link
Authentication (AuthN) - Authentication is the process of establishing the identity of a person or service looking to access a resource. It establishes if they are who they say they are.
Authorization (AuthZ) - Authorization is the process of establishing what level of access an authenticated person or service has. It specifies what data they're allowed to access and what they can do with it.
Azure Active Directory is a Microsoft cloud-based identity and access management service. Azure AD helps employees of an organization sign in and access resources:
External resources might include Microsoft Office 365, the Azure portal, and thousands of other software as a service (SaaS) applications.
Internal resources might include apps on your corporate network and intranet, along with any cloud apps developed by your own organization.
Azure AD provides services such as:
Azure AD is intended for:
With single sign-on (SSO), users need to remember only one ID and one password. Access across applications is granted to a single identity tied to a user, simplifying the security model.
By using a centralized identity provider, you'll have centralized the security controls, reporting, alerting, and administration of your identity infrastructure.
Azure Multi-Factor Authentication provides additional security for your identities by requiring two or more elements for full authentication. These elements fall into three categories:
Multi-factor authentication (MFA) comes as part of the following Azure service offerings:
Azure Security Center is a monitoring service that provides threat protection across all of your services both in Azure, and on-premises. Security Center can:
Azure Security Center versions

✔️ Walkthrough - Azure security center usage scenario
Link
Azure Key Vault is a centralized cloud service for storing your applications' secrets. Key Vault helps you control your applications' secrets by keeping them in a single, central location and by providing secure access, permissions control, and access logging capabilities.
Usage scenarios
Key Vault benefits
✔️ Walkthrough - Implement Azure Key Vault
Link
Azure Information Protection is a cloud-based solution that helps organizations classify and (optionally) protect its documents and emails by applying labels. Labels can be applied automatically (by administrators who define rules and conditions), manually (by users), or with a combination of both (where users are guided by recommendations).
You can purchase MSIP either as a standalone solution, or through one of the following Microsoft licensing suites: Enterprise Mobility + Security, or Microsoft 365 Enterprise.
Azure Advanced Threat Protection is a cloud-based security solution that identifies, detects, and helps you investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Azure ATP is capable of detecting known malicious attacks and techniques, security issues, and risks against your network.
Azure Advanced Threat Protection is available as part of the Enterprise Mobility + Security 5 suite (EMS E5), and as a standalone license.
Azure Policy is a service in Azure that you use to create, assign, and, manage policies. These policies enforce different rules and effects over your resources, so those resources stay compliant with your corporate standards and service-level agreements (SLAs).
It runs evaluations of your resources and scans for those not compliant with the policies you have created. Azure Policy also can automatically remediate resources and configurations that are deemed non-compliant, thus ensuring the integrity of the state of the resources.
There are three steps to creating an implementing an Azure policy.
An initiative definition is a set of policy definitions to help track your compliance state for a larger goal. Initiative assignments reduce the need to make several initiative definitions for each scope.
✔️ Walkthrough - Create an Azure policy
Link
Role-based access control provides fine-grained access management for Azure resources, enabling you to grant users only the rights they need to perform their jobs. RBAC is provided at no additional cost to all Azure subscribers.
To view access permissions, access the Access Control (IAM) blade in the Azure portal. This blade, shows who has access to an area and their role. Using this same blade, you can also grant or remove access.
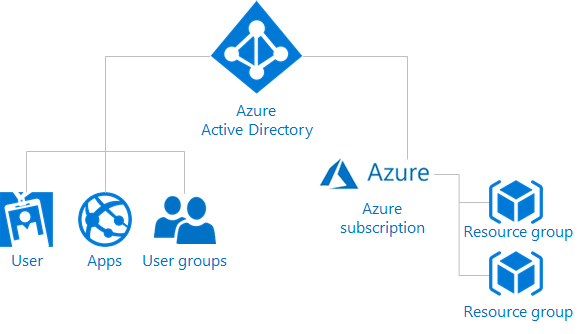
Using RBAC, segregate duties within your team and grant only the amount of access to users that they need to perform their jobs.
When planning your access control strategy, grant users the lowest privilege level that they need to do their work.
✔️ Walkthrough - Manage access with RBAC
Link
Resource locks help you prevent accidental deletion or modification of your Azure resources. You can manage these locks from within the Azure portal.
✔️ Walkthrough - Manage resource locks
Link
Azure Blueprints enable cloud architects to define a repeatable set of Azure resources that implement and adhere to an organization's standards, patterns, and requirements.
Azure Blueprint is a declarative way to orchestrate the deployment of various resource templates and other artifacts, such as: Role assignments, Policy assignments, Azure Resource Manager templates, Resource groups
Azure Blueprints are different from Azure Resource Manager Templates. When Azure Resource Manager Templates deploy resources, they have no active relationship with the deployed resources (they exist in a local environment or in source control). By contrast, with Azure Blueprint, each deployment is tied to an Azure Blueprint package. This means that the relationship with resources will be maintained, even after deployment. Maintaining relationships, in this way, improves auditing and tracking capabilities.
There are mainly three aspects to consider in relation to creating and managing subscriptions: Billing, Access Control, and Subscription limits.
Azure Monitor maximizes the availability and performance of your applications by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. It helps you understand how your applications are performing and proactively identifies issues affecting them and the resources they depend on.
Azure Monitor collects data from each of the following tiers:
As soon as you create an Azure subscription and start adding resources such as virtual machines and web apps, Azure Monitor starts collecting data.
Under the resource settings you can enable Diagnostics
Azure Service Health is a suite of experiences that provide personalized guidance and support when issues with Azure services affect you.
Azure Service Health is composed of the following:
Azure Monitor includes several features and tools that provide valuable insights into your applications, and the other resources they may depend on. Monitoring solutions and features, such as Application Insights and Container Insights, provide you with a deeper look into different aspects of your application and Azure services.
Azure Monitor features can be organized into four categories, these categories are: Analyze, Respond, Visualize and Integrate.
Visualizations, such as charts and tables, are effective tools for summarizing monitoring data and for presenting data to different audiences.
You'll often need to integrate Azure Monitor with other systems, and build customized solutions that use your monitoring data. Other Azure services can work with Azure Monitor to provide this integration.
Microsoft invests heavily in the development of robust and innovative compliance processes. The Microsoft compliance framework for online services maps their controls to multiple regulatory standards, which enables Microsoft to design and build services using a common set of controls. These controls streamline compliance across a range of today's regulations as they continue to evolve in the future.
Microsoft provides the most comprehensive set of compliance offerings (including certifications and attestations) of any cloud service provider.
🌐 List of Microsoft Compliance Offerings
The Microsoft privacy statement explains what personal data Microsoft processes, how Microsoft processes it, and for what purposes.
The Trust Center is a website resource containing information and details about how Microsoft implements and supports security, privacy, compliance, and transparency in all Microsoft cloud products and services. The Trust Center is an important part of the Microsoft Trusted Cloud Initiative and provides support and resources for the legal and compliance community.
The Service Trust Portal (STP) hosts the Compliance Manager service, and is the Microsoft public site for publishing audit reports and other compliance-related information relevant to Microsoft’s cloud services.
To access some Service Trust Portal materials, you must sign in as an authenticated user with your Microsoft cloud services account (either an Azure AD organization account or a Microsoft account), and then review and accept the Microsoft Non-Disclosure Agreement for Compliance Materials.
Compliance Manager is a workflow-based risk assessment dashboard within the Trust Portal that enables you to track, assign, and verify your organization's regulatory compliance activities related to Microsoft professional services and Microsoft cloud services such as Office 365, Dynamics 365, and Azure.
Compliance Manager provides ongoing risk assessments with a risk-based scores reference displayed in a dashboard view for regulations and standards. Alternatively, you can create assessments for the regulations or standards that matter more to your organization.
Azure Government is a separate instance of the Microsoft Azure service. It addresses the security and compliance needs of US federal agencies, state and local governments, and their solution providers. Azure Government offers physical isolation from non-US government deployments and provides screened US personnel.
Azure China 21Vianet is operated by 21Vianet is a physically separated instance of cloud services located in China, independently operated and transacted by Shanghai Blue Cloud Technology Co., Ltd. ("21Vianet"), a wholly owned subsidiary of Beijing 21Vianet Broadband Data Center Co., Ltd.
✔️ Walkthrough - Explore trust center
Link
Using Azure requires an Azure subscription which provides you with authenticated and authorized access to Azure products and services and allows you to provision resources. An Azure subscription is a logical unit of Azure services that links to an Azure account, which is an identity in Azure Active Directory (Azure AD) or in a directory that an Azure AD trusts.
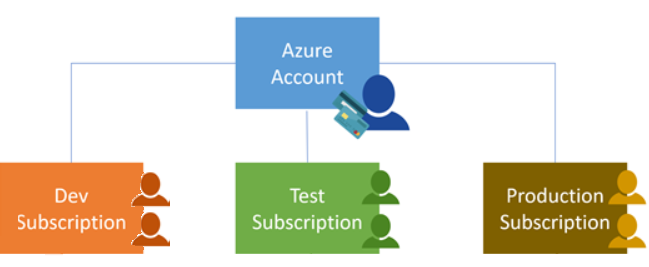
An account can have one subscription or multiple subscriptions that have different billing models and to which you apply different access-management policies.
There are two types of subscription boundaries that you can use, including:
You might want to create additional subscriptions for resource or billing management purposes. For example, you might choose to create additional subscriptions to separate: Environments, Organizational structures, Billing, Subscription limits, etc.
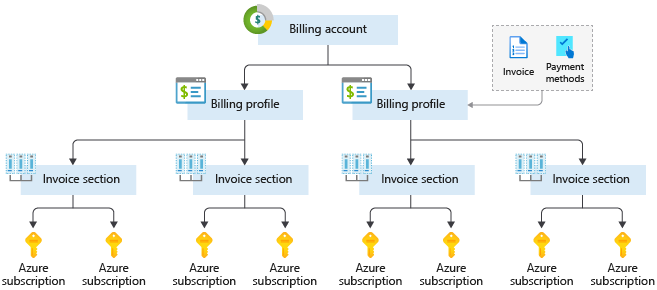
If you have multiple subscriptions, you can organize them into invoice sections. Each invoice section is a line item on the invoice that shows the charges incurred that month. For example, you might need a single invoice for your organization but want to organize charges by department, team, or project.
The following diagram shows an overview of how billing is structured. If you've previously signed up for Azure or if your organization has an Enterprise Agreement, your billing might be set up differently.
Azure offers free and paid subscription options to suit different needs and requirements.
🌐 Microsoft Azure Offer Details
The organizing structure for resources in Azure has four levels: management groups, subscriptions, resource groups, and resources. The following image shows the relationship of these levels i.e. the hierarchy of organization for the various objects
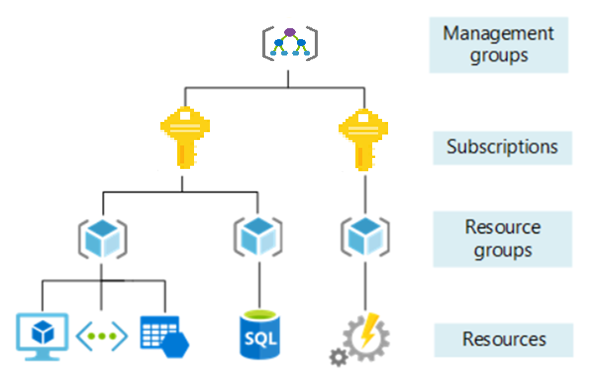
Management groups
These are containers that help you manage access, policy, and compliance
for multiple subscriptions.All subscriptions in a management group
automatically inherit the conditions applied to the management group.
Subscriptions
A subscription groups together user accounts and the resources that have
been created by those user accounts. For each subscription, there are
limits or quotas on the amount of resources you can create and use.
Organizations can use subscriptions to manage costs and the resources that
are created by users, teams, or projects.
Resource groups
A resource group is a logical container into which Azure resources like
web apps, databases, and storage accounts are deployed and managed.
Resources
Resources are instances of services that you create, like virtual
machines, storage, or SQL databases.
For customers that require a higher level of support there are four paid support plans available.
Azure Developer
Azure Developer offers a great option for individuals, small independent
developers, and ISVs who want to grow their business by focusing on
innovation instead of infrastructure. Included within this plan are all
the features of Azure subscription support along with unlimited 24x7
break/fix technical support through online submission, an 8 hr. maximum
initial response time for service incidents, and assistance with third
party technologies running on Azure.
Azure Standard
Azure Standard empowers small and midsize businesses to resolve issues by
providing technical support for all incidents. Included within this plan
are all the features of Azure Developer along with the added value of
callback phone support (up to three times a month) and a 2 hr. maximum
initial response time for highseverity incidents
Azure Professional Direct (ProDirect)
Azure ProDirect provides midsize and enterprise customers with service
delivery support from account managers, proactive monitoring of
high-severity incidents, and access to Microsoft resources and best
practices. Included within this plan are all the features of Azure
Standard along with enhanced services such as the following:
Premier Support
Premier Support delivers a comprehensive and flexible support plan for all
Microsoft services and products—whether on-premises, hybrid, or in the
cloud. Included within this plan are all the features of Azure ProDirect
along with these enhanced services:
There are three main customer types on which the available purchasing options for Azure products and services is contingent, including:
At the end of each monthly billing cycle, the usage values will be charged to your payment method and the meters are reset.
Resources are always charged based on usage. For example, if you de-allocate a VM then you will not be billed for compute hours, I/O reads or writes or the private IP address since the VM is not running and has no allocated compute resources. However you will incur storage costs for the disks.
When you provision an Azure resource, Azure creates one or more meter instances for that resource. The meters track the resources' usage, and each meter generates a usage record that is used to calculate your bill.
For example, a single virtual machine that you provision in Azure might have the following meters tracking its usage: Compute Hours, IP Address Hours, Data Transfer In, Data Transfer Out, Standard Managed Disk, Standard Managed Disk Operations, Standard IO-Disk, Standard IO-Block Blob Read, Standard IO-Block Blob Write, Standard IO-Block Blob Delete.
Costs are resource-specific, so the usage that a meter tracks and the number of meters associated with a resource depend on the resource type.
Azure usage rates and billing periods can differ between Enterprise, Web Direct, and Cloud Solution Provider (CSP) customers. Some subscription types also include usage allowances, which affect costs.
The Azure infrastructure is globally distributed, and usage costs might vary between locations that offer Azure products, services, and resources.
Billing zones help determine the cost of services you are using. Bandwidth refers to data moving in and out of Azure datacenters. Some inbound data transfers, such as data going into Azure datacenters, are free. For outbound data transfers, such as data going out of Azure datacenters, data transfer pricing is based on Zones.
A Zone is a geographical grouping of Azure Regions for billing purposes. the following Zones exist and include the sample regions as listed below:
The Pricing Calculator is a tool that helps you estimate the cost of Azure products.
Get a new estimate from the Pricing Calculator by adding, removing, or reconfiguring your selected products. You also can access pricing details, product details, and documentation for each product from the Pricing Calculator.
The Pricing Calculator provides estimates, not actual price quotes. Actual prices may vary depending upon the date of purchase, the payment currency you are using, and the type of Azure customer you are.
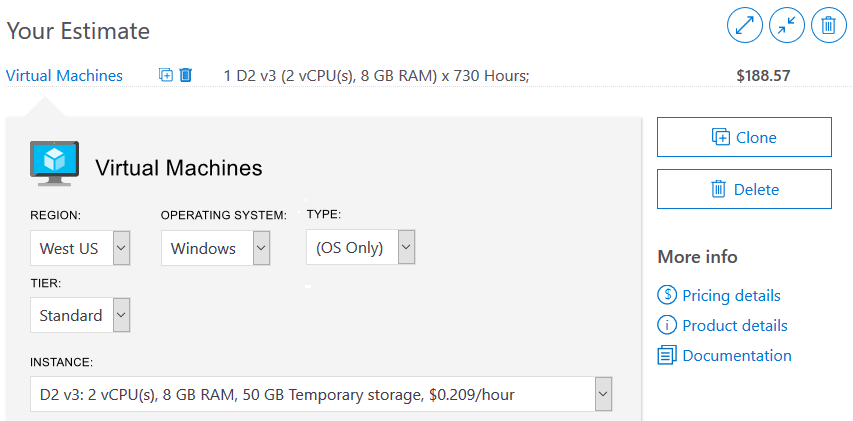
The options that you can configure in the Pricing Calculator vary between products, but basic configuration options include:
On the Pricing Calculator page, you'll see several tabs:
✔️ Walkthrough - Use Azure Pricing Calculator
Link
The Total Cost of Ownership Calculator is a tool that you use to estimate cost savings you can realize by migrating to Azure. To use the TCO calculator, complete the three steps that the following sections explain.
✔️ Walkthrough - Use Azure TCO Calculator
Link
The following best practice guidelines can help minimize your Azure costs.
Plan your Azure solution wisely. Carefully consider the products, services, and resources you need, and read the relevant documentation to understand how each of your choices are metered and billed. Additionally, you should calculate your projected costs by using the Azure Pricing and Total Cost of Ownership (TCO) calculators, only adding the products, services, and resources you need.
In an efficient architecture, provisioned resources match the demand for those resources. The Azure Advisor feature identifies unused or under-utilized resources, and you can implement its recommendations by removing unused resources and configuring your resources to match your actual demand.
Free trial customers and some credit-based Azure subscriptions can use the Spending Limits feature. Azure provides the Spending Limits feature to help prevent you from exhausting the credit on your account within each billing period. If you have a credit-based subscription and you reach your configured spending limit, Azure suspends your subscription until a new billing period begins.
The spending limit feature is not available for customers who aren't using credit-based subscriptions, such as Pay-As-You-Go subscribers. Note
Note: Azure spending limits are not the same as Subscription, Service, or Resource Group limits and quotas.
Azure Reservations offer discounted prices on certain Azure products and resources. To get a discount, you reserve products and resources by paying in advance.
The cost of Azure products, services, and resources can vary across locations and regions, and if possible, you should use them in those locations and regions where they cost less.
Keep up-to-date with the latest Azure customer and subscription offers, and switch to offers that provide the greatest cost-saving benefit.
Tags help you manage costs associated with the different groups of Azure products and resources. You can apply tags to groups of Azure products and resources to organize billing data.
Cost Management is an Azure product that provides a set of tools for monitoring, allocating, and optimizing your Azure costs.
The main features of the Azure Cost Management toolset include: Reporting
SLAs describe Microsoft's commitment to providing Azure customers with certain performance standards. There are SLAs for individual Azure products and services. SLAs also specify what happens if a service or product fails to perform to a governing SLA's specification.
A typical SLA specifics performance-target commitments that range from 99.9 percent ("three nines") to 99.99 percent ("four nines"), for each corresponding Azure product or service. These targets can apply to such performance criteria as uptime, or response times for services.
| SLA percentage | Downtime per year |
|---|---|
| 99 | 3.65 days |
| 99.9 | 8.76 hours |
| 99.95 | 4.38 hours |
| 99.99 | 52.56 minutes |
| 99.999 | 5.26 minutes |
The first column in the table below shows monthly uptime percentage SLA targets for a single instance Azure Virtual Machine. The second column shows the corresponding service credit amount you receive, if the actual uptime is less than the specified SLA target for that month.
Azure does not provide SLAs for many services under the Free or Shared tiers. Also, free products such as Azure Advisor do not typically have a SLA.
| Monthly Uptime Percentage | Service Credit Percentage |
|---|---|
| < 99.9 | 10 |
| < 99 | 25 |
| < 95 | 100 |
When combining SLAs across different service offerings, the resultant SLA is a called a Composite SLA. The resulting composite SLA can provide higher or lower uptime values, depending on your application architecture.
The combined probability of failure value is lower than the individual SLA values. This isn't surprising, because an application that relies on multiple services has more potential failure points.
99.95 percent × 99.99 percent = approx 99.94 percent
Conversely, you can improve the composite SLA by creating independent fallback paths. For example, if SQL Database is unavailable, you can put transactions into a Queue for processing at a later time.
Database *OR* Queue = 1.0 − (0.0001 × 0.001) = 99.99999 percent
Azure customers can use SLAs to evaluate how their Azure solutions meet their business requirements and the needs of their clients and users.
When creating an Application SLA consider the following:
Resiliency is the ability of a system to recover from failures and continue to function. High availability and disaster recovery are two crucial components of resiliency.
When designing your architecture you need to design for resiliency, and you should perform a Failure Mode Analysis (FMA).
Availability refers to the time that a system is functional and working. Maximizing availability requires implementing measures to prevent possible service failures. However, devising preventative measures can be difficult and expensive, and often results in complex solutions.
🌐 SLA summary for Azure services
✔️ Walkthrough - calculate composite SLAs
Link
Microsoft offers previews of Azure services, features, and functionality for evaluation purposes. With Azure Previews, you can test pre-release features, products, services, software, and even regions. Previews allow users early access to functionality. Additionally, users providing feedback on the preview features helps Microsoft improve the Azure service.
There are two categories of preview that are available:
You can access preview features that are specific to the Azure portal from the https://preview.portal.azure.com page.
Azure customers can provide feedback on the preview features they've tested by sending a smile in the portal. Or customers can post ideas and suggestions on the Azure portal feedback forum.
You can submit your idea in Azure portal feedback forum at https://feedback.azure.com page.
Once a feature is evaluated and tested successfully, it may release to customers as part of Azure.
Updates and new product featurese are available in Azure announcements blog.
Azure updates page provides information about the latest updates to Azure products, services, and features, as well as product roadmaps and announcements.
✔️ Walkthrough - Access Azure preview features
Link
📥 Microsoft Azure Virtual Training Day Fundamentals Day1.pdf
📥 Microsoft Azure Virtual Training Day Fundamentals Day2.pdf
🌐 Microsoft Certified: Azure Fundamentals
🌐 Exam AZ-900: Microsoft Azure Fundamentals
🌐 Learn: Cloud Concepts - Principles of cloud computing
🌐 Practice tests on Microsoft Azure Fundamentals (AZ-900)